Cyber vandalism disrupts businesses, damages reputations, and causes significant financial losses. The numbers are alarming: About 48% of SMEs have faced at least one cyber incident in the past year. The risks are growing, and businesses must stay ahead.
Holden Watne, Business Development Director, Generation IX, says “Cyber vandalism is not just about inconvenience—it’s about safeguarding your business’s operational continuity and trust”
This blog explains what cyber vandalism is, how it affects businesses, and actionable strategies to protect your systems.
Safeguard Your Business Against Cyber Vandalism
Prevent cyber vandalism from disrupting your digital assets and reputation. Act now with a customized security plan.
What Is Cyber Vandalism and Why It Matters
Cyber vandalism refers to deliberate attacks on digital assets to disrupt, deface, or destroy them. Unlike cybercrime, which seeks financial gain, cyber vandalism is often motivated by malice, activism, or personal agendas. Businesses of all sizes are at risk, making it critical to understand this threat.
A subset of this threat is data vandalism, where sensitive information is tampered with, leading to misinformation or operational disruption. Similarly, electronic vandalism covers attacks targeting hardware or connected devices.
How Cyber Vandalism Differs From Cybercrime
Though the two terms are often confused, cyber vandalism focuses on disruption, not theft. For example, a cybercriminal may steal sensitive data for profit, while a vandal’s goal is to corrupt or destroy it.
Businesses that don’t address both threats risk downtime, financial losses, and reputational damage.
Common Types of Cyber Vandalism
Cyber vandalism takes many forms, each with unique challenges. Understanding these can help you prepare for and prevent attacks.
- Malware Attacks
Malicious software, such as viruses, trojans, and worms, infiltrates systems to corrupt or delete files. Malware often spreads through phishing emails or unsecured networks, making robust endpoint security essential. - Website Defacement
Hackers replace a business’s web content with unauthorized messages or images. This not only disrupts operations but also damages your brand. Immediate detection and restoration processes are crucial to minimize impact. - Data Tampering
A form of data vandalism, this attack involves altering critical information, leading to operational errors or false reporting. Backups and access controls can limit this damage and restore normalcy quickly.
Digital Graffiti in the Modern Era
Vandalism has evolved into public-facing attacks like defacing websites or hacking social media accounts. These acts are often aimed at embarrassing businesses or pushing ideological messages. Protecting your online presence through advanced authentication and monitoring is non-negotiable.
| More articles you might like: |
|---|
The Real-world Impact of Cyber Vandalism
Cyber vandalism costs businesses time and money. The disruptions it causes can be widespread and expensive.
1. Revenue Loss
Downtime caused by attacks often halts transactions and services, leading to significant revenue drops. For small businesses, these losses can range from $137 to $427 per minute.
2. Repair Costs
Fixing vandalized systems requires expertise, whether through in-house IT teams or external consultants. The financial burden of repairs can strain businesses unprepared for such expenses.
3. Brand Damage
When customers see compromised systems or defaced websites, their trust in your business diminishes. Rebuilding this trust takes time and resources.
The Emotional Toll on Teams
The effects of computer vandalism extend beyond finances. IT teams face immense pressure to resolve issues quickly, often working long hours under stress. This toll can reduce productivity and lead to burnout, affecting overall business performance.
How to Prevent Cyber Vandalism
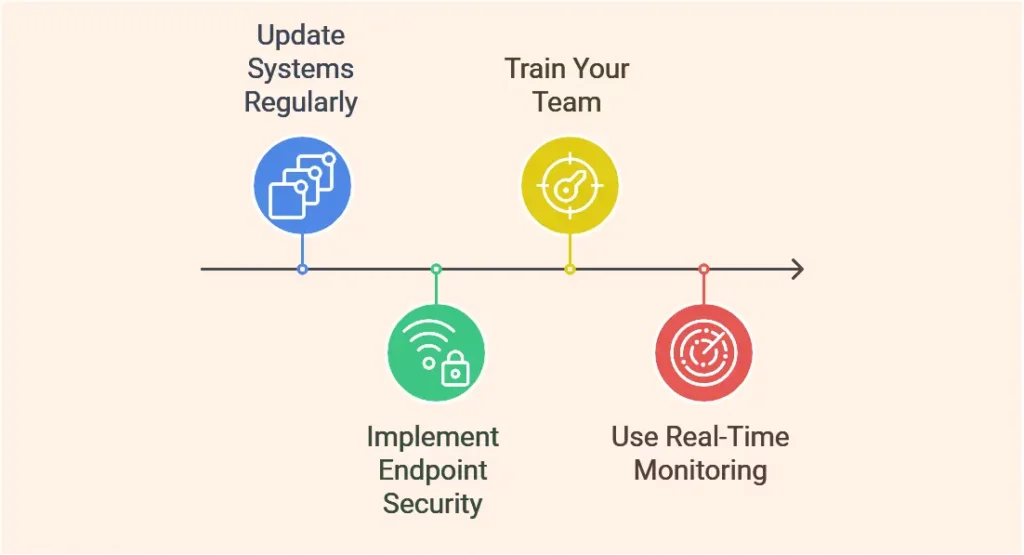
Proactive security measures are the cornerstone of protecting your business from cyber vandalism. By implementing the following steps, you can minimize risks and ensure business continuity.
- Update Your Systems Regularly: Outdated software is a gateway for cyber vandals. Regular updates patch vulnerabilities and enhance your defenses. Set automated updates or schedule manual checks to stay ahead.
- Implement Endpoint Security: Devices connected to your network are prime targets for electronic vandalism. Use antivirus programs, firewalls, and real-time monitoring tools to safeguard these entry points.
- Train Your Team: 56% of employees lack the knowledge to respond effectively when faced with a security incident. Employees are your first line of defense. Security training programs teach them to identify phishing attempts and report suspicious activity, reducing the likelihood of successful attacks.
- Use Real-Time Monitoring
Monitoring tools provide immediate alerts when unauthorized activities occur. This early detection helps mitigate damage, especially during data vandalism attempts.
The Role of Professional IT Services
Partnering with managed IT services or a virtual Chief Information Officer (vCIO) can strengthen your cybersecurity posture. These experts identify vulnerabilities, design tailored security plans, and ensure compliance with industry standards, reducing the chances of cyber vandalism.
Legal and Financial Responses to Cyber Vandalism
If your business falls victim to computer vandalism, taking swift and strategic action can limit its impact.
- Document the Attack: Keep detailed records of what happened, including timestamps, affected systems, and visible damage. This documentation is essential for insurance claims or legal proceedings.
- Notify Authorities: Report the incident to law enforcement or relevant regulatory bodies. These entities can provide guidance and investigate the attack, potentially deterring future incidents.
- Engage Cybersecurity Experts: Hire professionals to assess the damage and restore affected systems. Their expertise ensures your business can resume operations securely and efficiently.
The Legal Landscape
Many countries enforce strict penalties for cyber vandalism. Businesses should remain compliant with cybersecurity regulations to avoid fines and ensure accountability. Legal guidance may also be necessary to navigate these laws.
Proactive Tools to Combat Cyber Vandalism
Investing in the right tools can significantly reduce the risk of cyber vandalism. The table below outlines essential tools to safeguard your business and enhance your cybersecurity posture.
| Tool | Purpose | Example Tools |
|---|---|---|
| Endpoint Security | Protects devices from malware | Norton, McAfee, CrowdStrike |
| Multi-Factor Authentication | Adds a layer of login protection | Google Authenticator, Duo Security |
| Network Monitoring | Detects suspicious activity in real-time | SolarWinds, PRTG Network Monitor |
| Backup Solutions | Ensures data recovery after attacks | Veeam, Acronis, Backblaze |
Protect Your Digital Assets with Trusted Cybersecurity Solutions
Cyber vandalism, including electronic vandalism and data vandalism, presents an ever-growing challenge. By understanding its implications and investing in preventative measures, you can protect your business’s reputation, finances, and operational integrity.
| Trusted Cybersecurity Services Near You | ||
|---|---|---|
| San Jose | Irvine | Los Angeles |
Generation IX provides tailored cybersecurity services, with 25 years of experience serving LA businesses and a proven track record in transitioning to cloud solutions. Partner with us to secure your digital assets and maintain peace of mind.






