Security misconfigurations are one of the leading causes of preventable cyberattacks today. Failing to configure systems, applications, or networks properly leaves them exposed to attackers. In fact, 2023 saw a 72% increase in data breaches since 2021, which held the previous all-time record. Such vulnerabilities can lead to severe consequences, including data breaches, financial loss, and reputational damage.
As Holden Watne, Business Development Director, Generation IX says, “In today’s cybersecurity landscape, even small configuration mistakes can have disastrous consequences for businesses of any size.”
In this blog, we’ll explore what is a security misconfiguration, its common examples, and actionable steps you can take to avoid becoming a target.
Are Misconfigurations Putting Your Business at Risk?
Address vulnerabilities before they lead to a breach! 60% of data breaches stem from misconfigurations—don’t become another statistic.
What is a Security Misconfiguration?
A security misconfiguration occurs when systems, applications, or networks are set up with insecure settings, leaving them vulnerable to attacks. Whether it’s outdated software, default credentials, or mismanaged access controls, these issues open the door to unauthorized access.
A system can become exposed to security misconfiguration attacks when configurations are not reviewed or updated regularly. The attackers can exploit these vulnerabilities to gain access to sensitive data, compromise services, or manipulate the system for malicious purposes.
Common Security Misconfiguration Examples
Leaving Default Settings Unchanged
Many systems come pre-configured with default settings, such as usernames and passwords, that are easy to exploit if not changed. These defaults are widely known and readily available to attackers, making your system an easy target.
Misconfigured Permissions
Granting excessive permissions is another prime example of a security misconfiguration. When users or applications have more privileges than necessary, attackers can exploit these elevated privileges to access sensitive data or manipulate system configurations.
Outdated Software
One of the most common misconfigurations is running outdated software. Failing to apply security patches or updates leaves vulnerabilities that attackers can exploit, as they can target known flaws that have not been fixed.
Improper Cloud Configurations
As more businesses migrate to the cloud, security misconfiguration vulnerability in cloud environments has become a major risk. Misconfigured cloud storage, for example, can expose sensitive data to the public without the company’s knowledge.
Lack of Security Headers
Without proper HTTP security headers, web applications are at risk of attacks like cross-site scripting (XSS) or clickjacking. Always ensure that headers are correctly configured to protect your web applications from these threats.
Risks of Security Misconfigurations
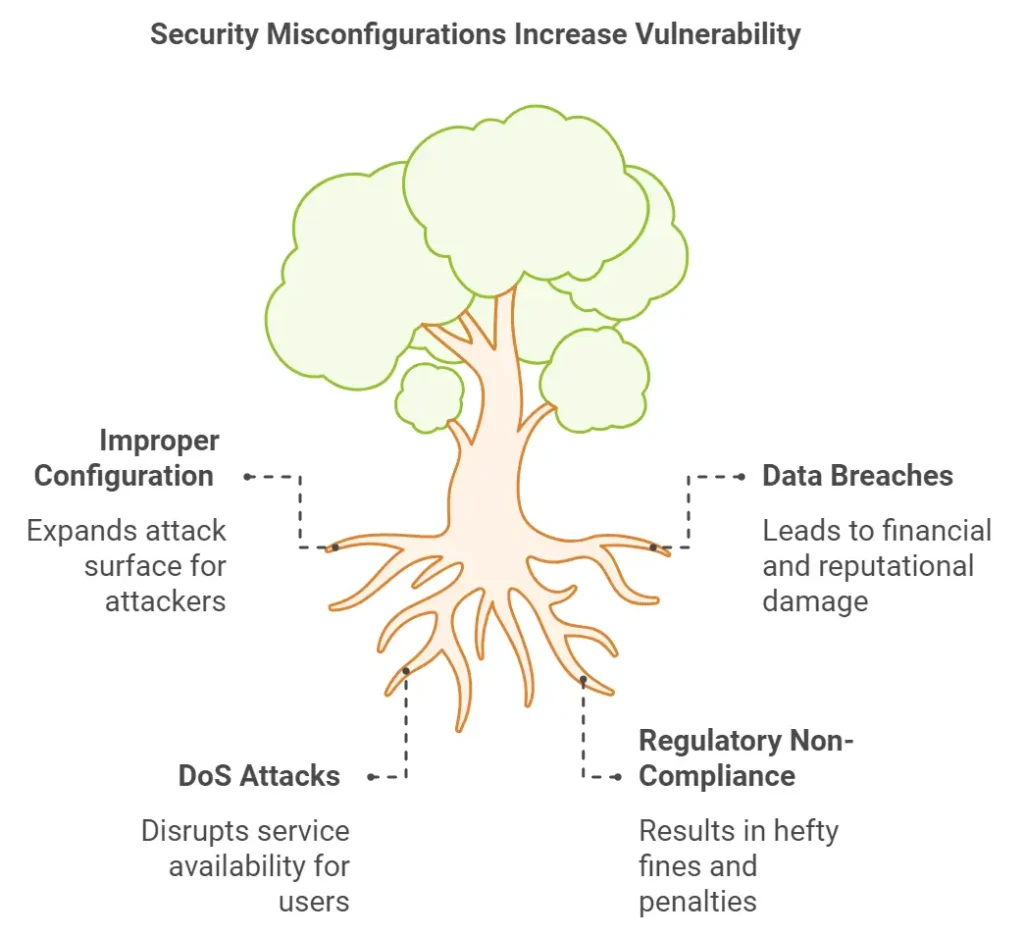
Expanding Attack Surface
Every security misconfiguration increases your attack surface. This means that every improperly configured system, application, or cloud resource becomes an entry point for attackers, giving them more opportunities to infiltrate your network.
Data Breaches
Did you know that the average lifecycle of a breach is 277 days from identification to containment? Data breaches are a frequent result of misconfigurations. One notable example is the Capital One breach in 2019, which exposed the personal data of over 100 million people due to a misconfigured web application firewall. These breaches can lead to significant financial and reputational damage to your business.
Denial of Service (DoS) Attacks
A misconfigured system can be exploited by attackers to launch Denial of Service (DoS) attacks, where they overwhelm your servers, making them unavailable to legitimate users.
Regulatory Non-Compliance
If your company handles sensitive data, like personally identifiable information (PII) or financial records, a security misconfiguration vulnerability could lead to violations of regulations such as GDPR, HIPAA, or PCI-DSS, resulting in hefty fines.
| More articles you might like: |
|---|
How to Prevent Security Misconfigurations
Conduct Regular Security Audits
Regular audits are crucial to identifying security misconfiguration examples within your systems. By conducting frequent reviews of your configurations, you can catch potential issues before they escalate into a breach.
Use Automated Security Scanning Tools
Automated tools like OpenVAS or QualysGuard can scan your systems for security misconfigurations and vulnerabilities. These tools help you identify weaknesses and offer solutions to fix them, reducing your risk of exposure.
Implement Strong Access Controls
One of the simplest ways to prevent security misconfiguration attacks is by implementing strict access control policies. Enforce the principle of least privilege, ensuring users and applications have only the permissions necessary to perform their roles.
Timely Patch Management
Ensure that all software, including third-party applications, is regularly updated. By keeping software up-to-date, you can minimize the risk of a successful attack exploiting known vulnerabilities.
Cloud Configuration Best Practices
When working in cloud environments, it’s essential to follow best practices. Always encrypt data, use proper authentication mechanisms, and closely monitor access control settings to avoid cloud security misconfiguration vulnerability.
Best Practices for Securing Your Systems
According to an article by CloudSecureTech, worldwide spending on data security has reached $81.6 billion.
Disable Unnecessary Features
By disabling unused features or services, you reduce the number of potential entry points for attackers. Limiting the number of active features makes it easier to manage your system’s security.
Enforce Strong, Unique Passwords
Never rely on default passwords or weak credentials. Ensure that all systems are configured with strong, unique passwords and multi-factor authentication (MFA) whenever possible.
Review and Harden System Configurations
After any system changes, always review the security configurations. Take additional steps to harden your configurations, such as disabling unnecessary services and closing unused ports.
Apply Role-Based Access Control (RBAC)
Role-based access control ensures that users are only granted the privileges they need. This helps to prevent unauthorized access to sensitive areas of your system and limits the damage that can be done if an account is compromised.
Top Security Misconfiguration Prevention Tips
| Prevention Tip | Description |
|---|---|
| Regular Configuration Reviews | Conduct routine audits to identify and correct misconfigurations. |
| User Access Control | Limit permissions to the minimum necessary for each role. |
| Standardization | Use templates for consistent configuration across systems. |
| Continuous Monitoring | Implement tools to track configuration changes in real-time. |
| Timely Updates | Regularly patch systems to fix known vulnerabilities. |
| Employee Training | Educate staff on best practices to prevent errors. |
Protect Your Business with Generation IX’s Expert Security Solutions
In the fast-evolving landscape of cybersecurity, security misconfigurations are an ever-present threat. From unpatched software to improper cloud setups, these oversights can lead to devastating attacks. You can protect your business from preventable risks by regularly auditing your systems, using automated tools, and enforcing strict configuration management practices.
| Discover Trusted Managed IT Services Near You: | |
| San Jose | Irvine |
| Los Angeles | |
Generation IX is a leading provider of security configuration audits and cybersecurity services. Contact us today to schedule a comprehensive audit and ensure your systems are securely configured.





